Hackers have targeted the gaming industry by carrying out billions of credential stuffing attacks against gaming websites within a 17-month period (November 2017 to March 2019), Akamai has claimed in its latest State of the Internet / Security Web Attacks and Gaming Abuse Report. Based on its findings, the US-based content delivery network and cloud service provider has put the gaming community “among the fastest rising targets for credential stuffing attacks and one of the most lucrative targets for criminals looking to make a quick profit.” To give an overview about the severity of the current situation, Akamai says that it saw a total of 55 billion credential stuffing attacks across all industries, out of which 12 billion were related to gaming industry alone.
Credential stuffing is a type of cyberattack where stolen account credentials, which generally consist of lists of usernames and/or email addresses and their corresponding passwords, are used to gain unauthorized access to user accounts through large-scale automated login requests directed against a web application. These credentials could be obtained from data breaches carried out against corporates. Akamai claims that the majority of the credential stuffing lists circulating on the darknet as well as on various forums use data that originated from some of the world’s largest data breaches.
A sample of the types of games where accounts can be purchased
“One reason that we believe the gaming industry is an attractive target for hackers is because criminals can easily exchange in-game items for profit. Furthermore, gamers are a niche demographic known for spending money, so their financial status is also a tempting target,” said Martin McKeay, Security Researcher, Akamai and Editorial Director of the State of the Internet/Security Report.
Akamai says that criminals target popular games looking for valid accounts and unique skins, in-game equipment, which are used to change the appearance of an item in a video game. Once a player’s account is successfully hacked, it can then be traded or sold. Apparently, hackers place more value on compromised accounts that are connected to a valid credit card or other financial resources. Once these accounts are compromised, the criminal can purchase additional items, such as currency used within the game, and then trade or sell the hijacked account.
“While gaming companies continue to innovate and improve their defenses, these organizations must also continue to help educate their consumers on how to protect and defend themselves. Many gamers are young, and if they are taught best practices to safeguard their accounts, they will incorporate those best practices for the rest of their lives,” McKeay added.
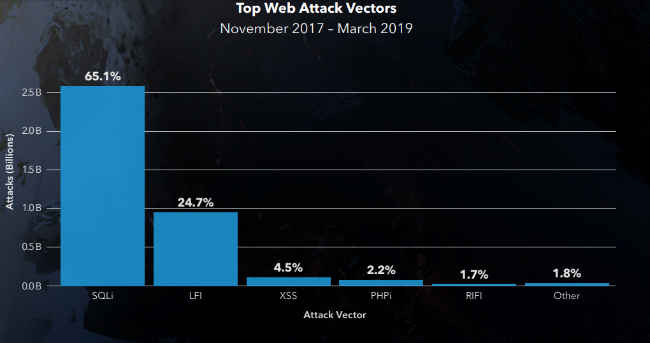
The Akamai report also reveals that SQL Injection (SQLi) attacks now represent nearly two-thirds (65.1 percent) of all web application attacks. It is followed by Local File Inclusion (LFI) attacks, which account for 24.7 percent of the total attacks. It also says that the SQLi and credential stuffing attacks are directly connected to each other in various cases. The company says that various breaches, from which credential lists are obtained, have SQLi as a root cause. In fact, earlier this year Akamai researchers discovered a video where viewers were instructed on how to conduct SQLi attacks against vulnerable websites.
Top source and target countries of application attacks (all verticles):The US tops the list of countries which are the source as well as the targets of the web attacks. Nearly 67 percent of application layer attacks target organisations based in the US. Russia is the second largest source of application attacks, but it’s nowhere to be found in the top 10 target countries. Similarly, China is ranked as the fourth highest source country, but is not among the top 10 target countries.
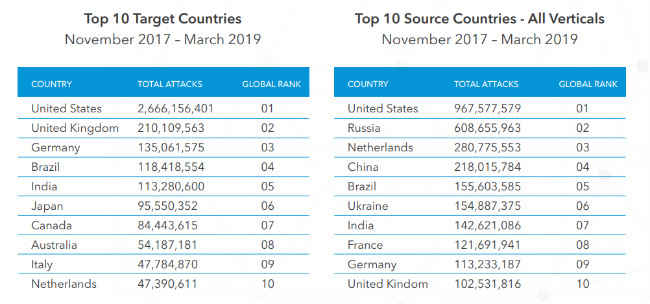
The UK is the second highest targeted country, but only tenth on the source country list. Japan, Canada, Australia and Italy are all also among the countries most targeted, but not on the top 10 source list. When it comes to India, it is placed on the fifth spot in the list of targeted countries and saw 113,280,600 attacks in the 17-month duration mentioned above. It is the seventh highest source country and carried out 142,621,086 application attacks.
Images source
from Latest Technology News http://bit.ly/2wSI41i









